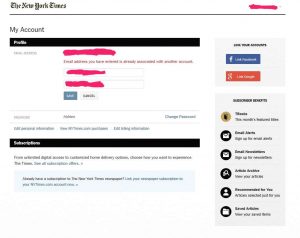
I have a problem with the New York Times “customer service.” My tablets and phone cannot access the electronic edition. They have dropped, one by one, over the past six months. I have tried to interface (!) with their phone representatives, but to no avail. What follows could sound trivial and mean spirited. So I dedicate it to the memory of Arthur Ochs Sulzberger. Diminished by the times, the Gray Lady is still worth saving.
Customer service is outsourced to “EGS Customer Care Incorporated”, who have the helpfully unavailable website, egscorp.com (click to enlarge): 
That it is unavailable may be no accident, as their phone number, (563) 285-2753, does not accept incoming calls. It actually has a voicemail that explains this, and helpfully asks the caller to “Please hang up.” My phone number received two calls from this number. I was not there to answer the phone. The caller promised to call later, but she did not.
This was preceded by two calls by me, one in the daytime and one at night, when I patiently tried to explain the problem. The first representative had the demeanor of a traffic court clerk. When, with icy tones, she asked me if “there is anything else I can do for you today?”, I was tempted to reply, “Please don’t bang the cell door when you lock it.” It seemed as if she had successfully dealt with the first problem:
Password cannot be changed.
But rather than allow me to change it, she went away and did something on my behalf, or so I thought. Had I known the perfidy of her solution, I might have gone (verbally) postal then and there. She “solved” the problem, without telling me, by appending the digit string “1234” to my existing email address. Now it was an email for nobody. But it took me several days to discover the deed.
Edit (5/31/17): With the apparent interest in this post, I’m adding some detail. On closing, the dialog with the above lady went like this:
Me: What about the tablets? They have me stuck on trial. After my 10 free articles... Her: Are you talking about the app or the browser? Me: The app. Her: You have to log into the browser first. Then you can log into the app.
Perhaps, in her Lewis Carroll world, the above is correct. It isn’t in mine. But she wore me down and disposed of me. Success! Time for a smoke.
The following evening, the rep was more down-home and more responsive. He instructed me to send a screenshot to customercare@nytimes.com, assuring me that, even without reference, they would know what it was for. So I did (click to enlarge):
The actual screen at the time said, “Unknown error.” So there is slight progress. We have an identifiable error. But NY TImes Customer Care does not assign case numbers. The following day, I received an email from Customer Care asking (paraphrased) “Why did you send this? What is your problem?” They had no way to reference it to the conversation of the previous evening.
Now “Carolyn” kicked in, calling from the EGS Corp. number that does not accept return calls:
Good morning. This is Carolyn with the New York times, and I was given your name and some information that you're having some problems with your replica addition and that you haven't been able to log into the new York times. I'd like to talk to you and walk you through and make sure we could get you going on this. I apologize. I'm not able to reach you this morning. I will keep trying through the day as I get some time because I would like to help you get this resolved. I will like I said call you. I'm trying to think maybe a couple hours are try again. I don't know if you work outside your home or are out doing errands, but I will try again a little bit later. I only work til 2 o'clock. As again I said I apologize for reaching you please have a great rest of the day, and thanks for using york times. Bye. Bye.
Replica Edition? That is way down on the list. If only I could get my tablets to work! Caroline did not try again that day. Her standards are a little loose. Instead, she called the morning of the following day:
Good morning. This is Carolyn with the New York times. I'm calling you again and leaving a message this time. I apologize. I have missed you. I'm trying to help you get. Your replica addition first of all not all the information you've received is correct. if you use your home delivery dot nytimes.com and log in and select replica addition in the lower two thirds of the page you can you don't have to do anything special, but if you're trying to use the device which is what I've read from several of the emails. You need to make sure you have the login from press reader and the information that on press reader can provide you and you talked about having an exit in executable file for that. You can contact newspapers direct by emailing them at New York times at support dot newspaper direct.com. They do only answer emails. They are in Canada, but they do respond very well we've had several subscriptions within our group that we use just to check that out and they do respond as well again. I apologize it was not able to reach you today. I am still going to try to reach you so I can talk to you, but I wanted to give you this information so we can get you started. I also reset your password so that I could make sure that you were able to use the website to get to your replica Dishan, and so your password is now 1 2 3 4 5 6. but you can login with that and change it at my account. Please have a great rest of the day, and thanks for using your time. Bye. Bye.
More yada yada about Replica, a latter part of my wish list. She reset my password. With anticipatory sadness, I accessed my profile to see if magic had occurred (click to enlarge):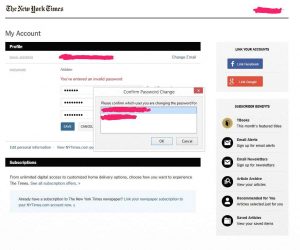
I now have two conflicting accounts. Nothing works. I had actually received a customer survey, which I answered like a sympathetic sap, because I didn’t want another job to go to Mumbai. I gave it damnation with faint praise. Now I would go with straight damnation.
I feel sorry for an American institution which is trying so hard to fill its quintessential role, sabotaged by an “EGS Corp.” whose principal talent is disposing of loyal customers. Objectively,
- Without case numbers, it is impossible to follow up.
- Customers are never escalated to second level support. Maybe there isn’t any.
- EGS Corp. hides from contact by phone or website.
- The system they have devised gives the appearance of diligence, but is actually a fraud.
But the New York Times is not innocent. That one of the greats of investigative journalism could miss this issue suggests internal decay. Nobody is asking the right questions of the right people. The Gray Lady is getting old.
This experience goes with the zeitgeist exemplified by U.S. Airways, Wells Fargo, VW Emissions, GM ignition switches, “let-em-die” healthcare, meaningless slogans like “customer support your way“, clip-art representing nonexistent people, and so forth. The collective “We” matters little. But perhaps it’s always been a fiction. The question deserves debate.
I’ll wait another week till I the end the subscription. I’ve subscribed since 1996.